Two Factor Authentication on O2
All O2 cluster logins from outside of the HMS network require two-factor authentication.
The Two Factor Authentication FAQ has quick answers to your more specific questions.
Or read below for a broader overview of 2-factor authentication.
| If logging into O2 from... | Will two factor authentication be required? |
|---|---|
HMS wired network connection in an HMS on-campus building (Note that this may exclude certain cases where labs from HMS affiliates have office space in an HMS building like the NRB) | No |
| HSDM and HSPH networks | No |
When logged into the HMS VPN - from anywhere (Please do NOT copy large files to/from O2 when on VPN.) | No |
"HMS Secure" wireless network | No |
| ------------------------------------------------------------------------- | ------ |
| "HMS Guest" wireless network | Yes |
| Other Harvard networks (FAS, etc) | Yes |
| Networks at all other HMS affiliates (hospitals, etc) | Yes |
| Any other external network (home, etc), NOT using the HMS VPN | Yes |
an HMS system (even on campus) which has a public-facing IP address (This is mostly for web and other application servers, not your desktop) | Yes |
| within O2... | Will two factor authentication be required? |
| ssh/copy from O2 login nodes to transfer.rc.hms.harvard.edu | Yes |
| ssh from one login node to another login node | Yes |
| ssh from one transfer node to another transfer node | Yes |
| ------------------------------------------------------------------------- | ------ |
| ssh/copy from compute node to transfer.rc.hms.harvard.edu | No |
| copy from interactive job to/from transfer.rc.hms.harvard.edu | No |
| copy batch job to/from transfer.rc.hms.harvard.edu | No |
Summary
Two factor authentication is required to access both regular login servers and file transfer servers:
- o2.hms.harvard.edu
- Includes all O2 login servers: login01.o2.rc.hms.harvard.edu , login02.o2.rc.hms.harvard.edu, etc...
- transfer.rc.hms.harvard.edu
With two-factor authentication, your O2 login additionally requires a secondary validation such as a security code sent to your cell phone or a code generated by an application such as Duo Mobile.
- HMS requires it for resetting your HMS ID password and other services such as the HMS VPN.
Setting up the DUO application for HMS
If you already use DUO with the HMS VPN, then you are all set for O2.
If you use DUO with Harvard Key but not HMS yet, you still need to set up a separate DUO HMS profile.
The easiest way is to try logging into O2 via ssh. If you are not yet registered, you will be prompted to register with a unique URL, as shown below:
DESKTOP:~$ ssh abc123@o2.hms.harvard.edu Password: [input your account password] Please enroll at https://api-2f8a17a9.duosecurity.com/portal?code=443789224a30udsihdj8a&akey=DAIUI3JAB2FHDJKS7MJRQ0G
You can also visit the following page for how to register your device/phone for use with DUO at HMS.
Once you are enrolled in DUO for HMS:
Login (using an SSH application as usual) to O2: o2.hms.harvard.edu
- Follow instructions for inputting your security code:
- Enter either "1" or "push" to authenticate via DUO
- Enter either "2" or "phone" to authenticate via response to a voice call
- Enter either "3" or "sms" to get a code via a SMS text message
The example below is for user "abc123" using the "Duo Push" method.
DESKTOP:~$ ssh abc123@o2.hms.harvard.edu The authenticity of host 'o2.hms.harvard.edu (134.174.159.25)' can't be established. ECDSA key fingerprint is SHA256:4/hjkdsfdsaF*asdhfksdalhfklhfj/dS54. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'o2.hms.harvard.edu,134.174.159.25' (ECDSA) to the list of known hosts. Password: [input your account password] Duo two-factor login for abc123 Enter a passcode or select one of the following options: 1. Duo Push to XXX-XXX-1234 2. Phone call to XXX-XXX-1234 3. SMS passcodes to XXX-XXX-1234 Passcode or option (1-3): 1 Pushed a login request to your device... Success. Logging you in... Welcome to O2 (Orchestra 2)!
Command Line Tool (SFTP/SCP/etc.) and Graphical Tool (Filezilla, WinSCP) logins:
By default non-interactive commands like scp/sftp/rsync or applications like FileZilla/WinSCP/MobiKwik etc. will not prompt for a choice between "push | call | sms" and require a default Duo authentication method of "push" or "call" to be set up. If this is not set, the command/application will simply hang forever or timeout after a few seconds. Please see the section below for directions on setting up a default authentication method. For examples and tips on using these tools with 2FA, please see our FAQ.
How to setup default DUO Method using DUO_PASSCODE environment variable
You can setup a default DUO setting by doing either of the two following methods.
Using O2
- to be set on your o2 cluster
.bashrcor.bash_profile - values: phone, push, sms, sms1, phone1, push1, sms2, push2, phone2.
- If you set DUO_PASSCODE variable as mentioned below, then you will not be prompted for any type of login either ssh or scp/sftp/rsync etc.
- It is not recommended to use sms with DUO_PASSCODE variable, because you won't be given a prompt to enter sms code, so the login attempt will fail.
- NOTE: By choosing this method, you'll not be prompted for regular ssh commands as well, if you just want auto push for non-interactive commands choose the other method for setting default DUO.
Example:
#login to o2 normally DESKTOP:~$ ssh abc123@o2.hms.harvard.edu Welcome to O2 (Orchestra 2)! ... [abc123@login06]:~ $ # THIS HAS TO BE DONE ONLY ONCE [abc123@login06]:~ $ echo 'export DUO_PASSCODE=phone' >> $HOME/.bashrc #CHECK WHETHER .bashrc IS UPDATED [abc123@login06]:~ $ tail -1 $HOME/.bashrc export DUO_PASSCODE=phone #now logout from o2 [abc123@login06]:~ $ logout Connection to o2.hms.harvard.edu closed. #NOW, TRY SCP/SFTP/RSYNC DESKTOP:~/$ sftp abc123@o2.hms.harvard.edu Connected to o2.hms.harvard.edu. sftp> quit quit #NOW, TRY SSH TO A SERVER DESKTOP:~/$ ssh o2.hms.harvard.edu Reading $DUO_PASSCODE... Calling your phone... Dialing XXX-XXX-1234... Answered. Press 1 on your phone to log in. Success. Logging you in... Welcome to O2 (Orchestra 2)! ... [abc123@login06]:~ $ #Note: if you have '[ -z "$PS1" ] && return' in your .bashrc, the instructions above will not work. You need manually add 'export DUO_PASSCODE=phone" above '[ -z "$PS1" ] && return'. So the commands should be: export DUO_PASSCODE=push [ -z "$PS1" ] && return
Using secure.med.harvard.edu
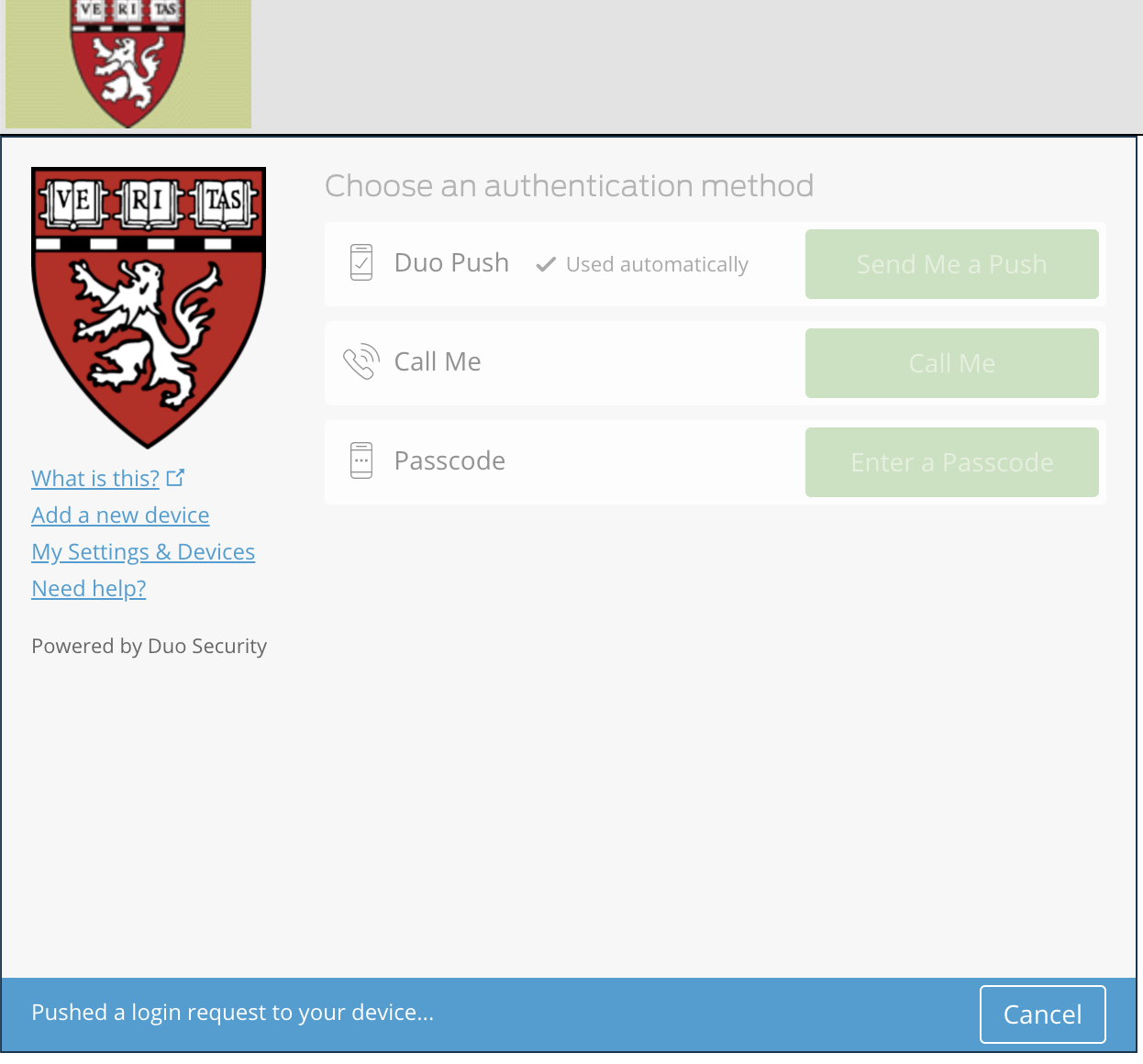
login to secure.med.harvard.edu using any browser of your choice, after entering your HMS ID and password, you'll be landed on a page shown like below,
Click cancel at the bottom of the prompt so that you don't get re-directed.
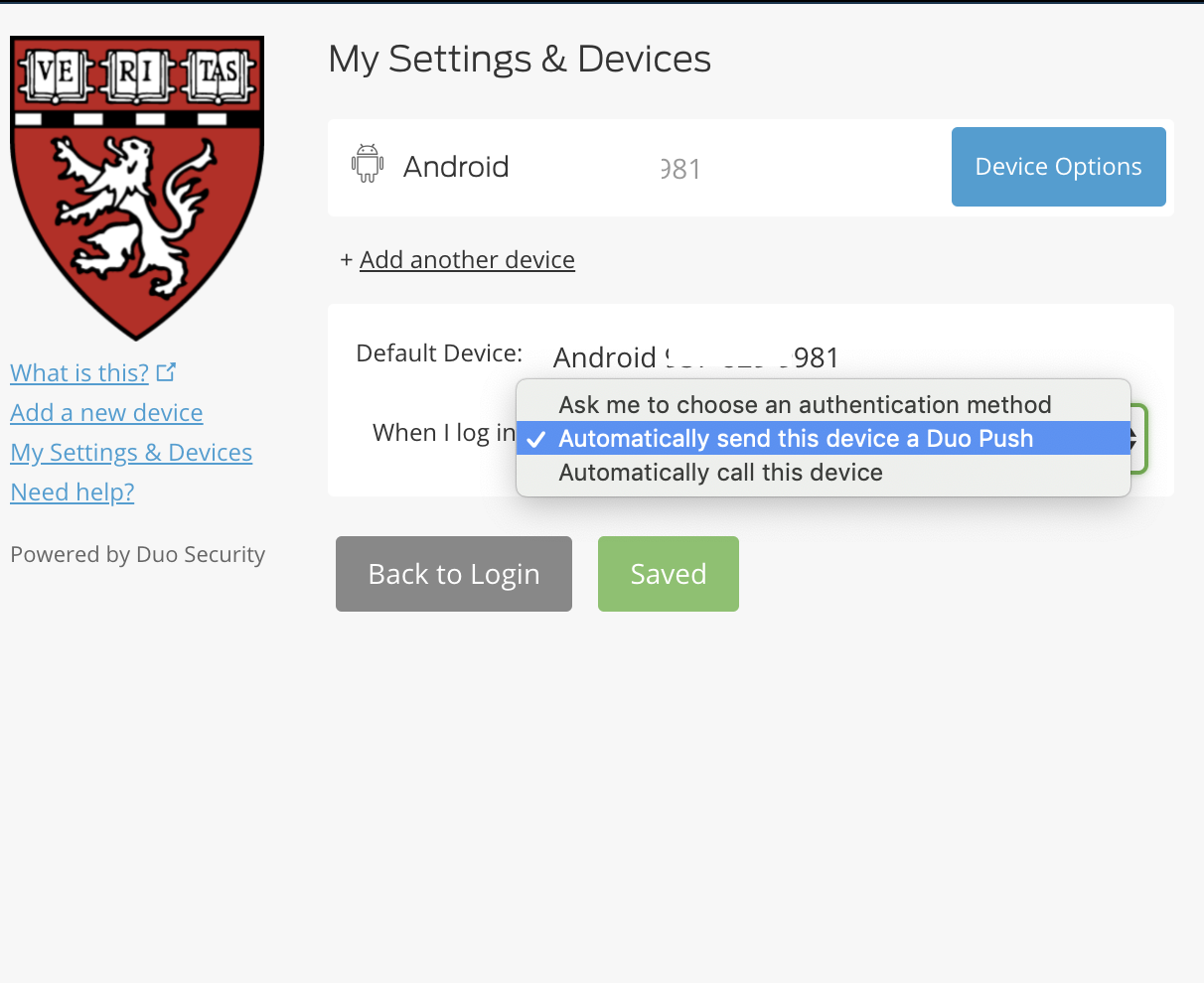
Now click My Settings&Devices on the left hand side bar, now you've to approve/accept your 2fa so that you'll land on a page something like this below.
Now you can choose your default method and save it. That should do it!
The next time you do scp/sftp/any non-interactive commands you'll get a default prompt on your default chosen method.
- NOTE: By choosing this method, you'll still get prompted for regular ssh commands, if you just want auto push for ssh commands as well choose the o2 method for setting default DUO.
For Windows Users:
To set up your DUO_PASSCODE environment variable, consult a page like this: https://www.computerhope.com/issues/ch000549.htm (this may require administrator access on your local machine).
This may be a good time for you to transition away from PuTTY if that is your primary method of connection to O2. We have been recommending "native" terminal emulator applications such as MobaXterm, or for savvy Windows 10 users, Windows Subsystem for Linux. The reason for this is that setting the above environment variable (DUO_PASSCODE) is somewhat involved on Windows as opposed to on OS X or other *nix systems due to there not being easy access to a terminal (and cmd.exe and powershell.exe are not suitable replacements most of the time). Applications such as MobaXterm superimpose a *nix-like terminal over your Windows installation, and you can navigate your system much like you would navigate O2. Once you have one of these types of applications set up, you can follow the above example verbatim instead of having to do complex menu navigation to accomplish the equivalent result. MobaXterm also has a built-in X server, so you no longer need a separate program running to perform X11 forwarding (e.g. Xming), as well as a built in ftp browser, so you don't need programs like Filezilla or WinSCP either. We recommend any of the following over PuTTY:
EASY -
MobaXterm - https://mobaxterm.mobatek.net/ (the free version should be all you need)
MEDIUM/HARD (but far more flexible) -
Windows Subsystem for Linux (for Windows 10 only) - https://docs.microsoft.com/en-us/windows/wsl/install-win10
Cygwin - https://www.cygwin.com/
WSL and Cygwin require some level of user competence to configure, so if that is not of interest, we definitely recommend MobaXterm as the drop-in replacement.
Support
Please let HMS Research Computing know if you experience any trouble with using two-factor authentication: rchelp@hms.harvard.edu